A private hosted zone is a container that can respond to internal DNS queries for a domain or its subdomains and it can be attached to one or more VPCs.
For example, if you have an HTTP server running on an EC2 instance on a VPC, and you want to have a name for this HTTP service such as webserver.example.com, you can create a private hosted zone for example.com on AWS Route 53, and add an internal record, meaning the name webserver.example.com can resolve to a private IP address like 172.31.93.204 when the request is initiated from within the VPC.
AWS has DNS Resolvers for each VPC, usually they're the .2 address on the IP pool of the VPC. For example, if you have a VPC with 172.31.0.0/16 CIDR, the DNS Resolver on that VPC is 172.31.0.2.
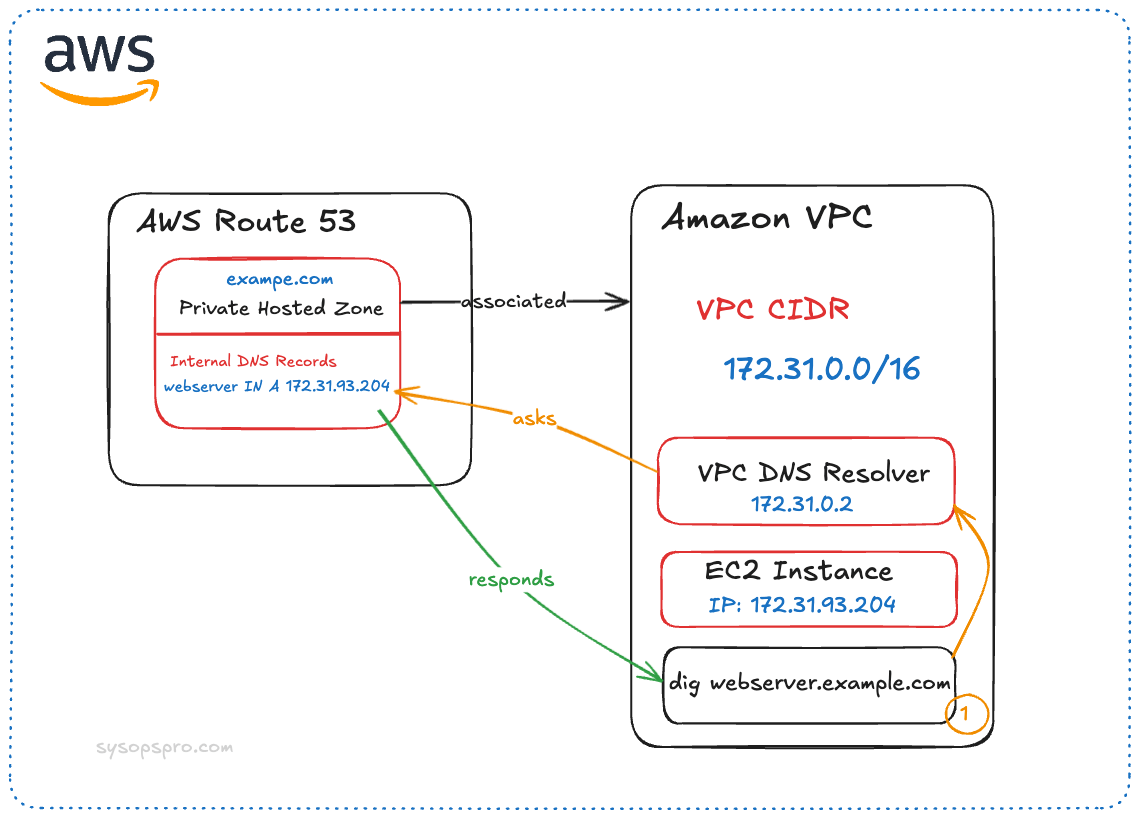
If you query a private hosted zone from outside of the VPCs it's associated with, the DNS query will not hit the AWS DNS Resolvers and will be routed to the internet. Therefor, DNS records in a Private hosted zone is not discoverable from the internet.
AWS attaches a bunch of Name Servers (NS) to your private AWS Hosted Zone, but they are only there because it's mandatory for a hosted zone to have Name Servers. In reality, those Name Servers are never used.
Those Name Servers are:
- ns-0.awsdns-00.com
- ns-512.awsdns-00.net
- ns-1024.awsdns-00.org
- ns-1536.awsdns-00.co.ukYou can combine Private Hosted Zones with Public Hosted Zone to route internel vs internet traffic to different servers for the same domain or subdomain. This is called Split-View DNS and it's explained in a later section in this article.
Prerequisites
- Your VPCs must have enabled the
DNS hostnamesandDNS resolutionattributes. We have covered checking this later in this tutorial.
Creating a Private Hosted Zone
To create a Private Hosted Zone, go AWS Console and head over to the Route 53 service.
-
From the left navigation panel, select "Hosted Zones".
-
Choose "Create hosted zone" and enter the following information:
- A domain name such as example.com. This domain cannot be queried from the internet because we are using Private Hosted Zone. Therefore, you can choose any domain name.
- For the Type, make sure you select "Private hosted zone"
- Attach VPCs to the hosted zones. When you attach a hosted zone to a VPC, resources in that VPC can query DNS records in this hosted zone.
- Click "Create hosted zone" button to finish creating the hosted zone.
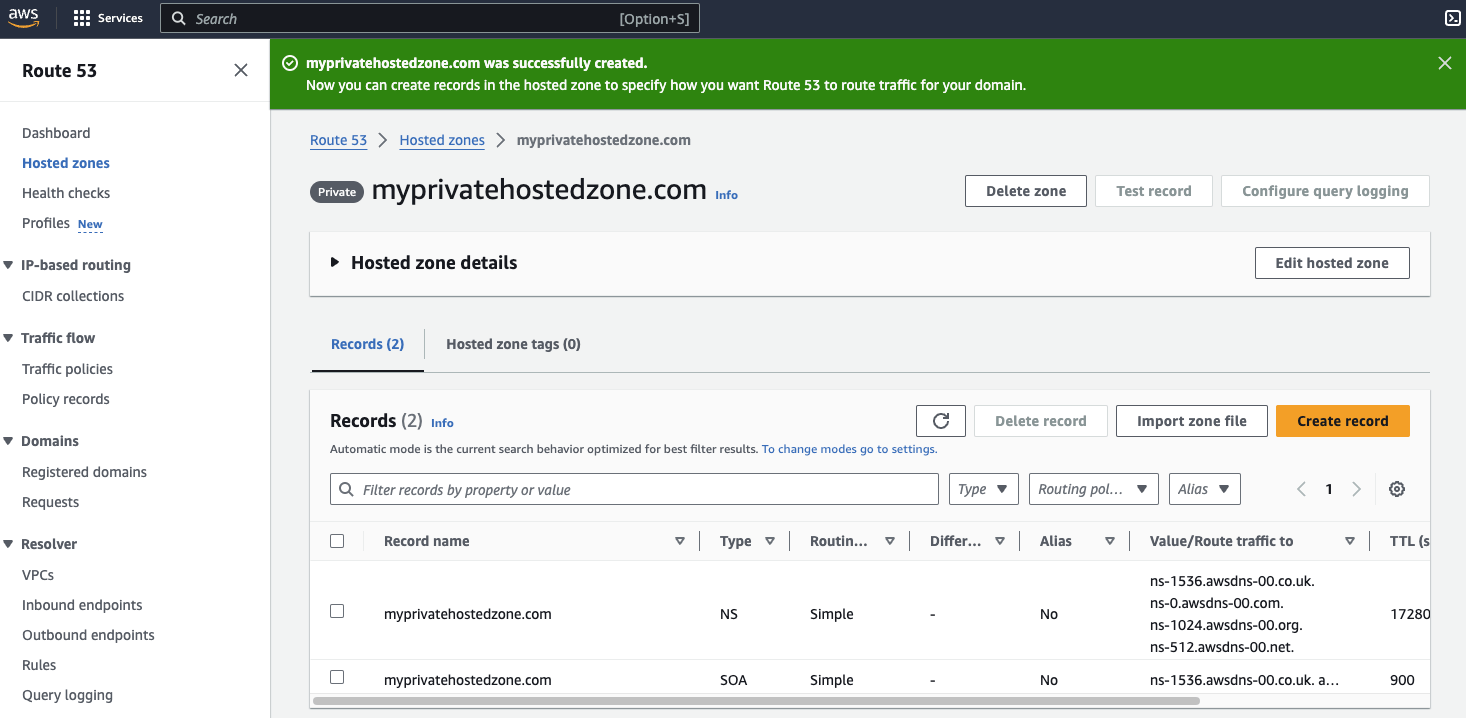
Notice that AWS has added the two NS and SOA records by default.
Creating Private DNS Records
The Private Hosted Zone we just created can now hold DNS records for our dummy domain myprivatehostedzone.com.
We can create DNS records in our Private hosted zone and resolve them to private resources in the associated VPCs.
I have an EC2 server running and I have installed nginx on the server. I have allowed port 80 on my Security Group and currently the web server is available from the internet using the EC2 instance's public IP address.
However, we want this service to be only available from within VPC (internal traffic only). To achieve this, we can make an internal DNS record on our Private Hosted Zone to map our dummy domain to the EC2 instance's Private IP address.
So the first step is to get the private IP address of the EC2 instance. In my case, it's 172.31.93.204.
So heading over to my Private hosted zone, I can click on "Create record" button
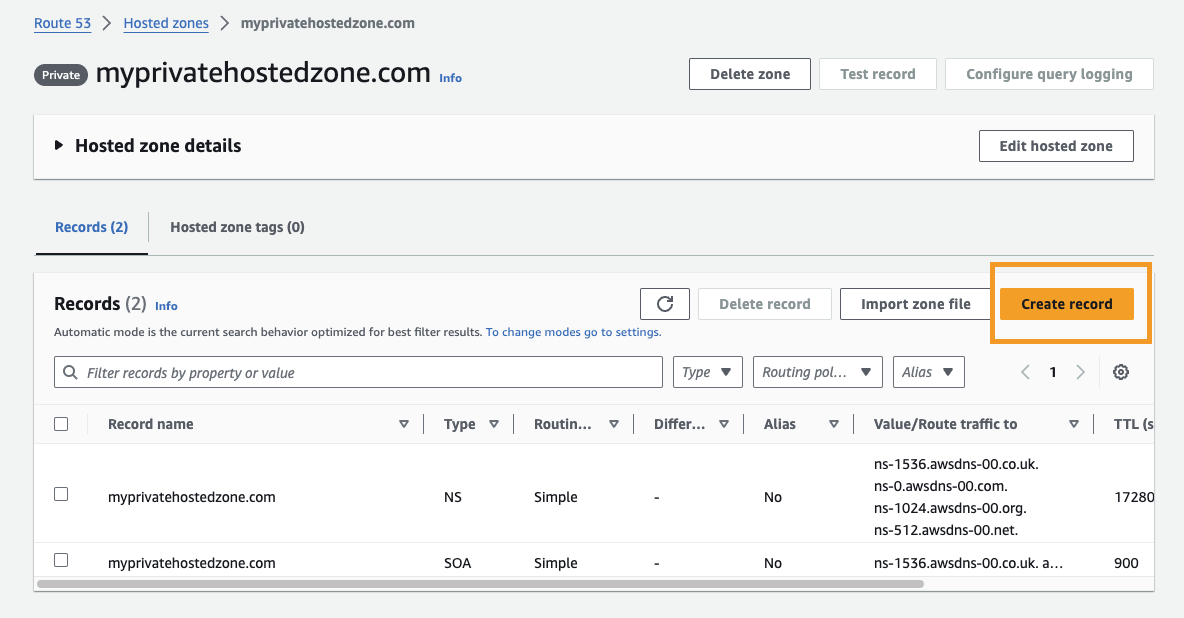
When creating a record, you can specify a subdomain such as nginx.myprivatehostedzone.com, or if you want to resolve the domain root, such as myprivatehostedzone.com, you can leave the subdomain box empty and provide the private IP address of the EC2 instance as the value.
The record type is going to be an A record since we will resolve the domain to a private IP address. The TTL can be 300 as default or modify as need and keep the Routing Policy as Simple Routing.
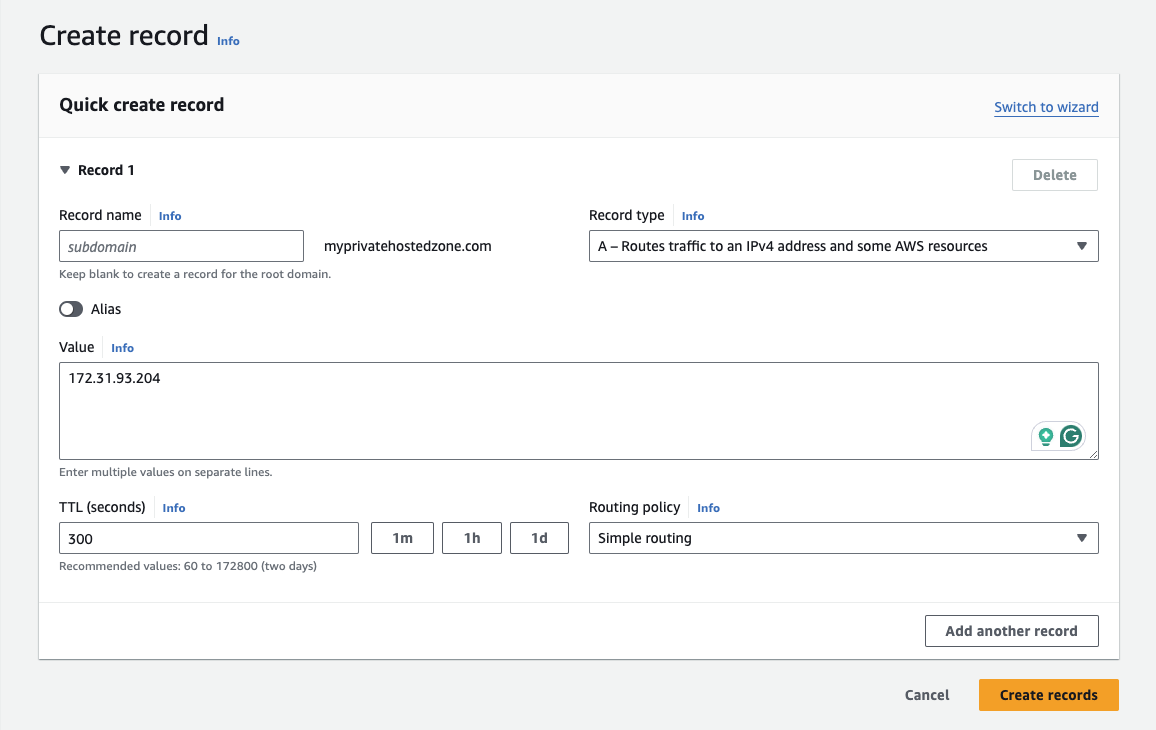
Once filled, click "Create records".
Enable DNS Hostnames on Your VPC
The prerequisite for enabling Private Hosted Zones on Route 53 is that your VPCs associated with the hosted zone must have DNS hostnames property enabled.
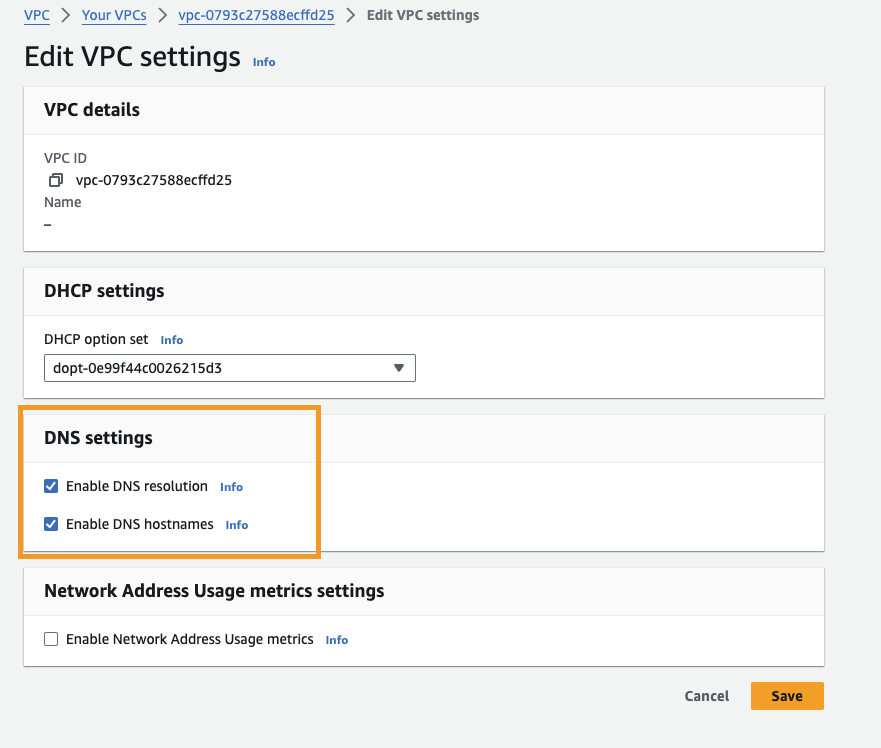
To check this, you can go to your VPC and under Details tab check for "DNS hostnames" property.
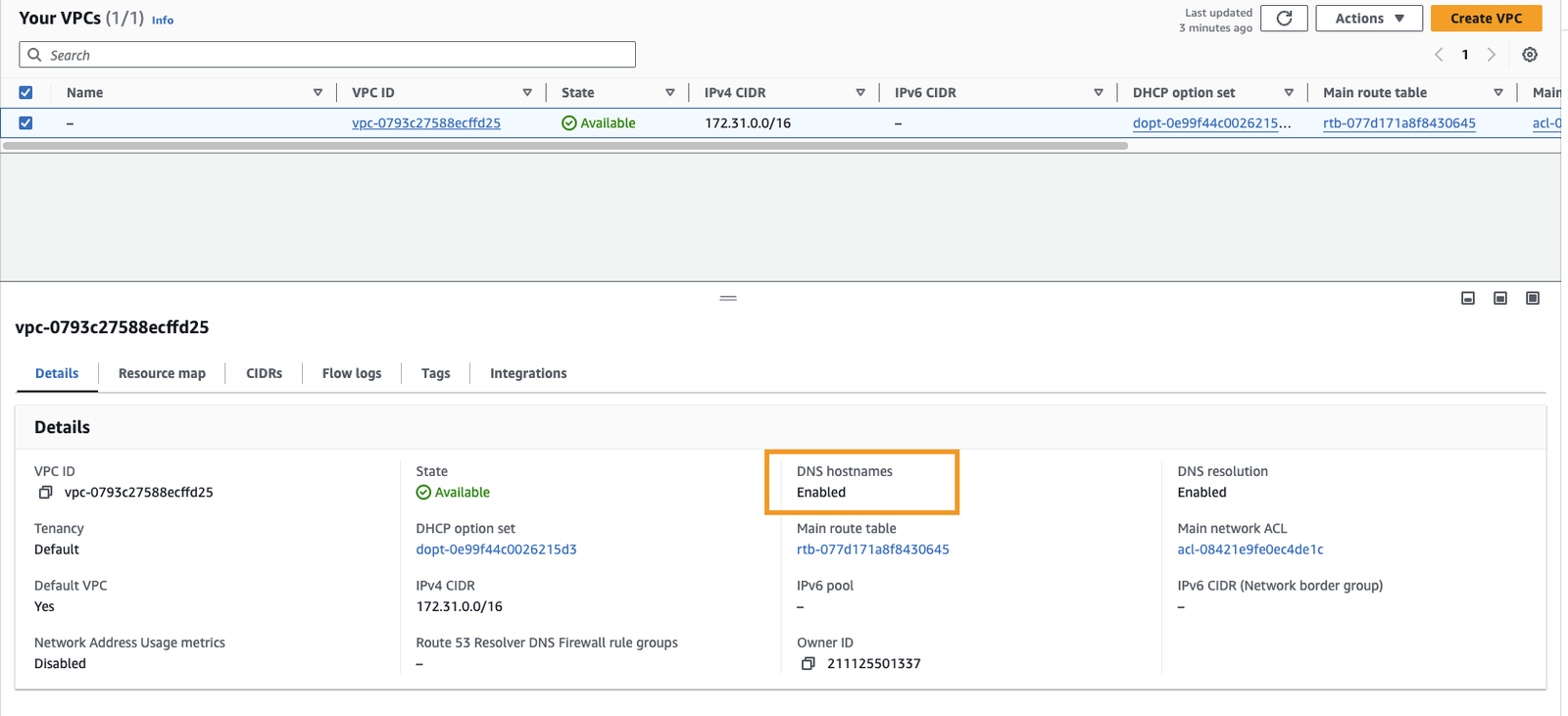
If it's Disabled, you can enable it by going to Actions > Edit VPC Settings and tick the DNS settings checkboxes
Testing the Private Hosted Zone records
If you go to myprivatehostedzone.com from the internet, your query will not reach the Hosted Zone to resolve the name to the IP address. In addition, we are utilizing a private IP address and that means the service is not accessible via the internet. All the connections remain within the VPC in this set up.
However, the DNS name myprivatehostedzone.com should be resolvable from within the VPC.
To test our newly created DNS record, we can SSH to our EC2 server and run a dig or nslookup query for the domain myprivatehostedzone.com.
nslookup myprivatehostedzone.com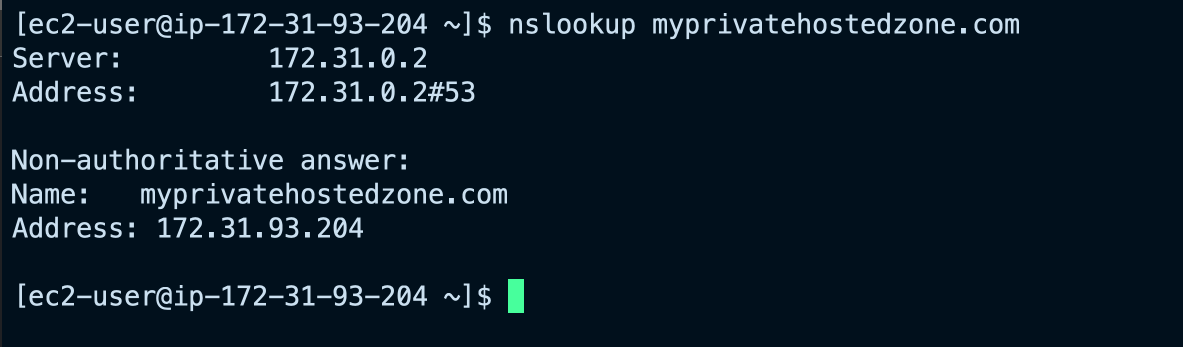
As you can see, our DNS record for myprivatehostedzone.com is resolvable to the private IP address we assigned to it.
Also notice the Server property in the output of nslookup command that shows which DNS server responded to the DNS query. It points to 172.31.0.2 and that is the AWS VPC DNS Resolver IP. We know that because it has the .2 as the last octet in the VPC network IP pool.
You can test the HTTP connection to the web server using the domain name with tools such as cURL.
curl -Is http://myprivatehostedzone.com | head -1And you should see a "HTTP 200 OK" response:
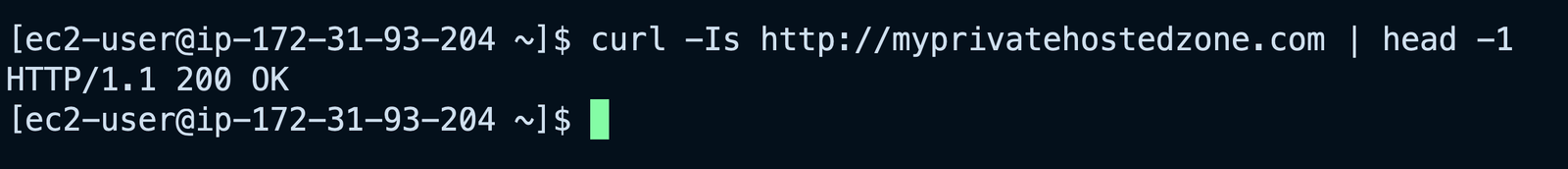
If you try to resolve this domain from outside VPC, you will not get any response - of course. That's because the DNS entry is nowhere in the public DNS servers. It only exists within our VPC and it can only be queried using the AWS DNS Resolver within the VPC.
Accessing Nginx Server From the Browser
Is it even possible to access myprivatehostedzone.com from a browser?
Yes, that's possible if your have a VPN Server in your VPC that you can connect to. When you connect to a VPN server such as OpenVPN, your traffic will be routed via the server. Because the VPN server is located within your VPC, you can configure it to use the AWS DNS Resolver as its DNS server. This is typically configured in /etc/resolv.conf file.
With this setup, if you visit myprivatehostedzone.com from your browser, the VPN server is going to ask the AWS DNS Resolver for the A record of myprivatehostedzone.com. The AWS DNS Resolver will look into the Private Hosted Zone for the DNS records and resolve the record to the private IP address.
Creatiing Split-View DNS records
A Split-View DNS involves using a combination of two hosted zones, a public hosted zone for handling internet (external) DNS queries, and a private hosted zone with the same name responding to queries that are initiated from within the VPC i.e Internal queries.
For example, you might serve different web content or enforce different authentication mechanisms based on whether a query originates from inside your network or from the internet.
In a Split-View DNS setup, you must have the domain registered under your name or organization and you cannot use a dummy domain name as we did with the myprivatehostedzone.com domain.
With Split-View, you should create two identical hosted zones for the same domain. A public hosted zone for handling external (internet) DNS queries and a private hosted zone for handing internal DNS queries.
The DNS records in these zones can be identical in terms of record types and names, but they should contain different values appropriate to their audience.
I don't have the myprivatehostedzone.com domain registered, so I cannot do a demo on Split-View DNS, unfortunately.
Read more about Split-View DNS here.
Conclusion
You can use AWS Route 53 Private Hosted Zones to resolve DNS records to private resources such as private IP addresses or DNS names. The domain you create in a Private Hosted Zone does not need to be a registered domain and it can never be queried from the internet. The internal queries will be routed to the private hosted zones via the VPC DNS Resolvers.






